Uncomplicated Firewall (UFW) is a command-line interface for manipulating iptables rules in a simplified and easy-to-understand way. One of the early tasks you should perform once Debian is installed is to secure your system’s ports. Rather than using your classic iptables rules, you can use easy-to-remember ufw rules to set your firewall up. That’s fantastic for new network experts and sysadmins who just want to get their Debian 12 systems secure ASAP.
In this article, you will be able to follow steps for several ways to install UFW on Debian 12 to make sure you have an easy way of securing your system.
Table of Contents
- How to Install UFW on Debian 12
- Post-Installation Configuration
- How to Uninstall UFW on Debian 12
- Troubleshooting Common Issues
- Conclusion
How to Install UFW on Debian 12
UFW is a good combination of function and ease of use and is the perfect choice to secure a Debian 12 system. For the case of one server or multiple systems, UFW provides a user-friendly way to manage your firewalls. If you are currently connected to your server via SSH, be careful about authorizing UFW rules, or you’ll end up locked out of your server.
Let’s follow the easiest method:
Method 1: Install UFW Using APT Package Manager (Recommended)
The easiest way to set up UFW on Debian 12 is by using the APT package manager since UFW is included in the official Debian repositories. APT leans on the official repositories for Debian so that UFW is downloaded securely and properly integrates with system dependencies.
Step 1: Update Package Lists
First, update the package list to get the latest versions of your repository:
sudo apt update
Step 2: Install UFW
First, install UFW through the apt command:
sudo apt install ufw
Step 3: Verify Installation
Verify if UFW is correctly installed:
sudo ufw --version
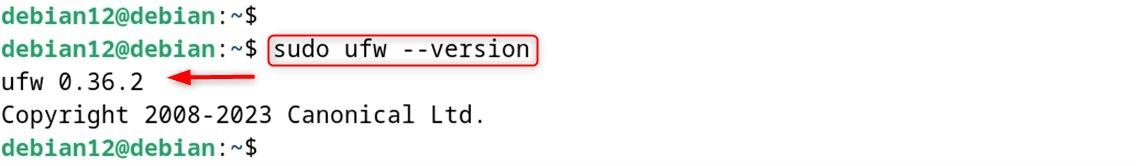
An output like that should get written to your terminal.
Step 4: Check UFW Status
Check the status of UFW:
sudo ufw status

Initially, UFW will be inactive (disabled) after installation.
Method 2: Install UFW from Source Code
This method will install UFW directly from the source code. This is for users who prefer to install the latest development version or to customize the installation. For those who are more experienced and desire the newest features, or if you want to further customize the install, then you can compile UFW from source.
Step 1: Install Dependencies
Install the necessary build tools and stuff:
sudo apt update
sudo apt install build-essential python3-dev python3-setuptools git
Step 2: Download UFW Source Code
First of all, clone the UFW repository or get the source code. Or you can also get the recent release through the UFW website:
git clone https://git.launchpad.net/ufw
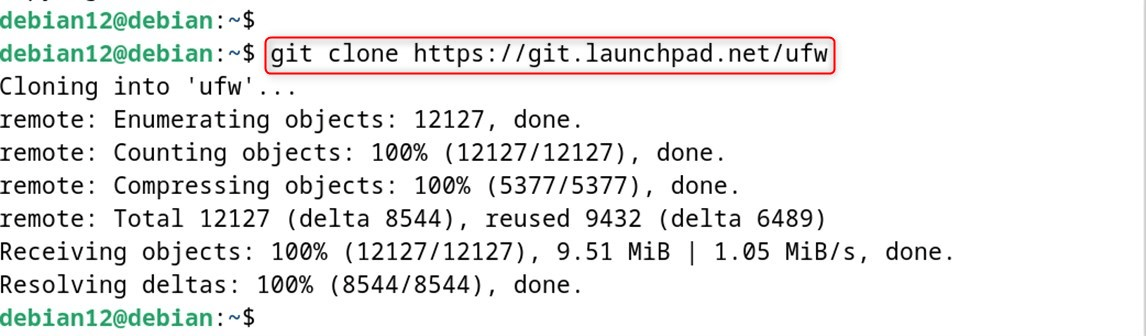
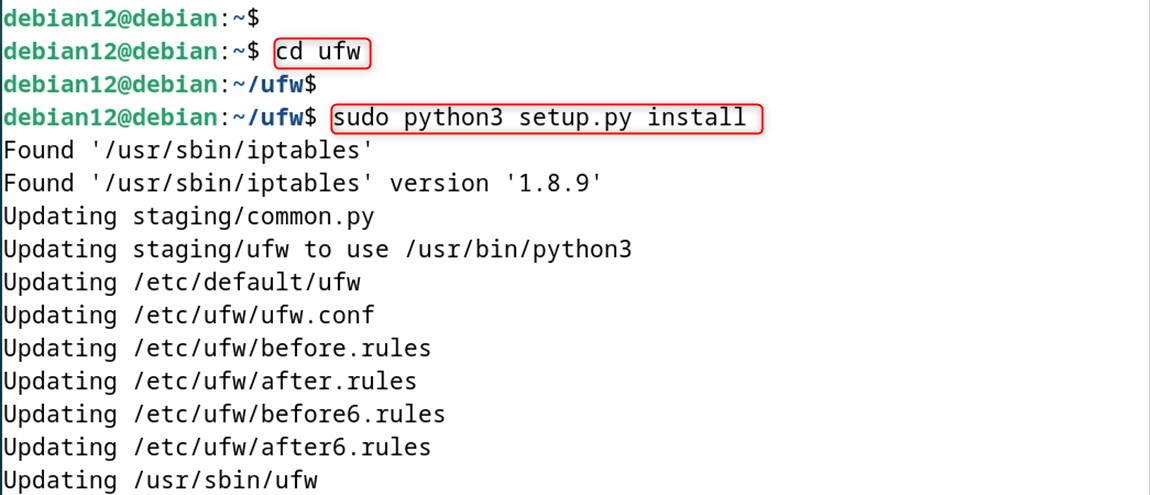
Step 3: Build and Install
Unzip ufw.zip and build/install it from source:
cd ufw
sudo python3 setup.py install
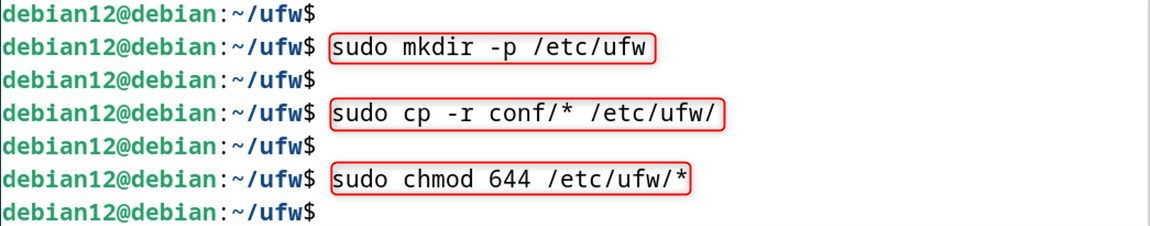
Step 4: Set Up UFW
Then, after installation, set up the required directories and files:
sudo mkdir -p /etc/ufw
sudo cp -r conf/* /etc/ufw/
sudo chmod 644 /etc/ufw/*
Step 5: Verify Installation
Make sure UFW is installed:
ufw version

Method 3: Install UFW Using Snap Package Manager
And finally, this last method, which is probably my favorite, is to install the UFW via snap.
Step 1: Install Snapd (if not already installed)
Snap is another package manager that can be used to install UFW on Debian 12.
sudo apt install snapd
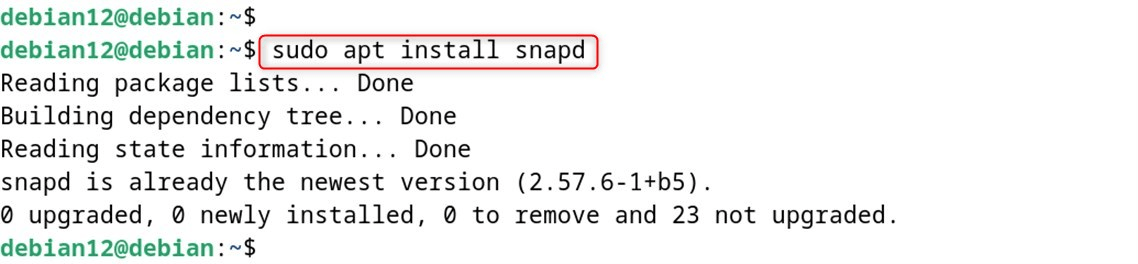
Step 2: Install UFW via Snap
After that, install ufw utility through the following command:
sudo snap install ufw
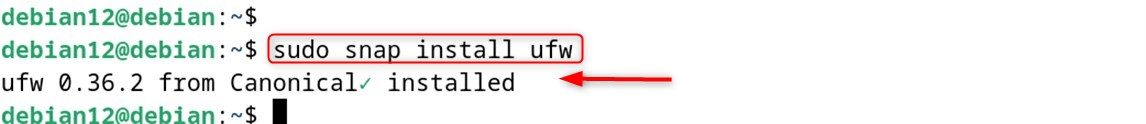
Step 3: Verify Installation
Finally, verify the installed version through the following line:
sudo ufw --version
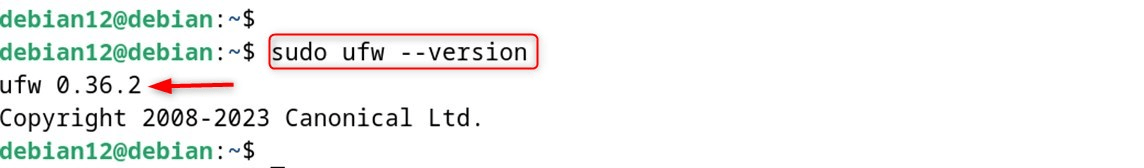
Snap UFW may behave slightly differently from APT UFW.
Post-Installation Configuration
Once you have the UFW installed with any of the above methods, you’ll want to configure it correctly:
Now that you have UFW on your system, set it up with these few simple commands:
Enable UFW
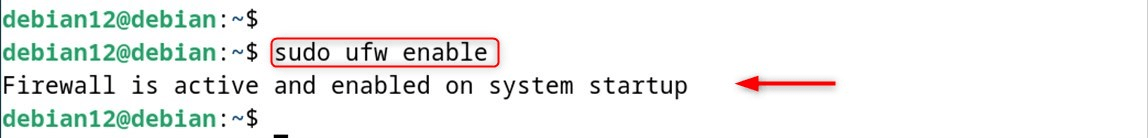
Now, enable the utility with sudo privileges:
sudo ufw enable
Set Default Policies
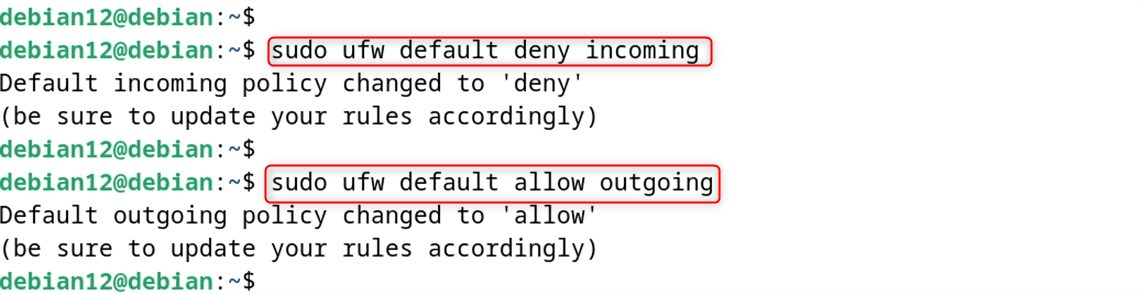
Set up the default policies (recommended for most users):
sudo ufw default deny incoming
sudo ufw default allow outgoing
Allow SSH (Important for Remote Access)
If you want to be able to use SSH for possible remote access, you must allow it before turning on UFW:
sudo ufw allow ssh
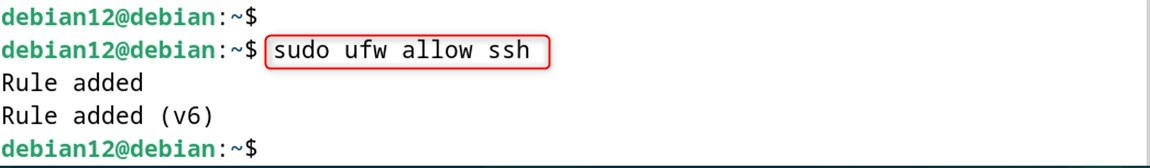
Or allow a specific SSH port:
sudo ufw allow 22/tcp
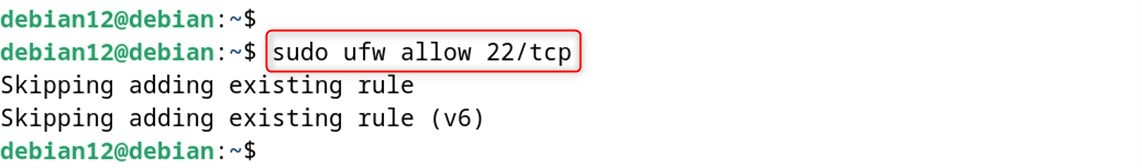
Check UFW Status
Verify your UFW configuration:
sudo ufw status verbose
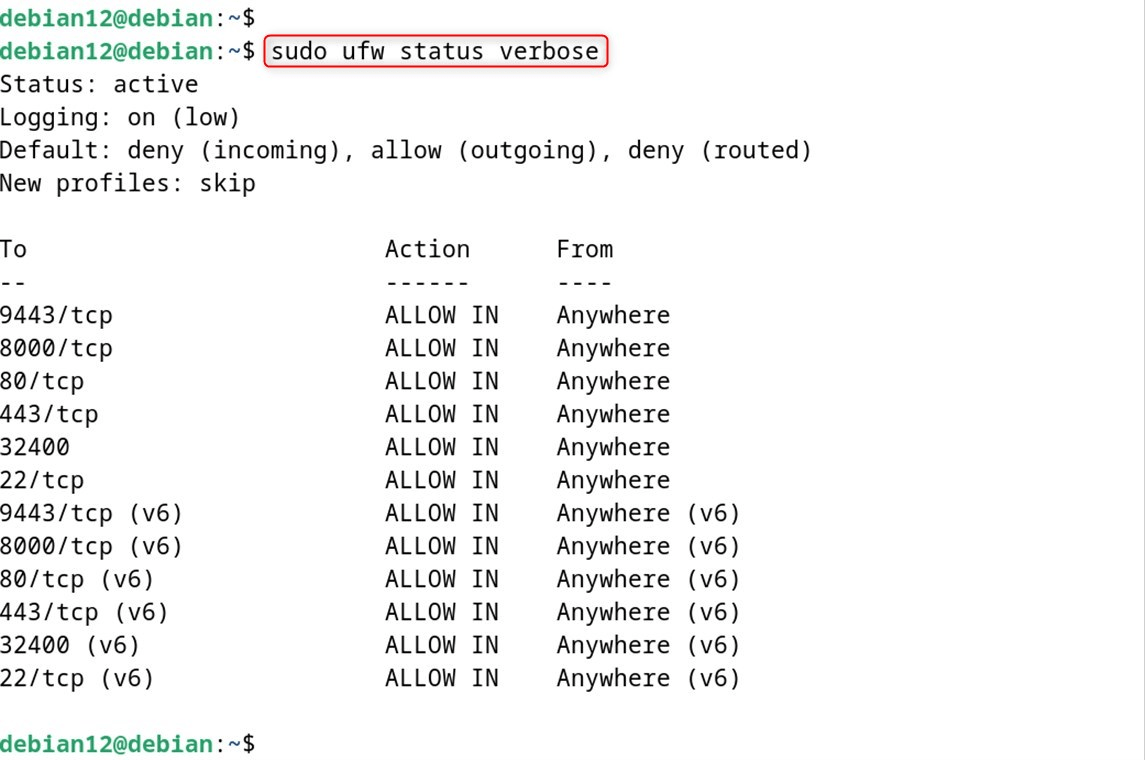
How to Uninstall UFW on Debian 12?
If you need to remove UFW:
sudo apt remove ufw
To also remove configuration files:
sudo apt purge ufw
Troubleshooting Common Issues
For more advanced setups and cool UFW features, see the official UFW documentation and carefully consider your security needs when opening firewall ports. Let’s follow some common issues:
Issue 1: UFW Command Not Found
If you are on a VPS and running UFW and your UFW command is simply not being found, the server’s firewall paint may be beginning to chip.
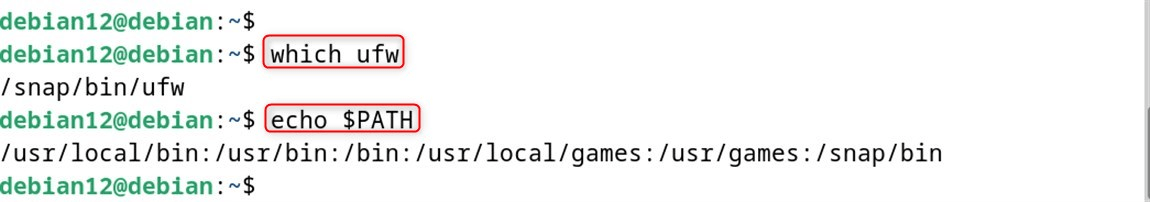
If you get “command not found,” then make sure that UFW is installed, and your PATH is set up correctly:
which ufw
echo $PATH
Issue 2: Permission Denied
You should be using sudo while giving commands to UFW:
sudo ufw status
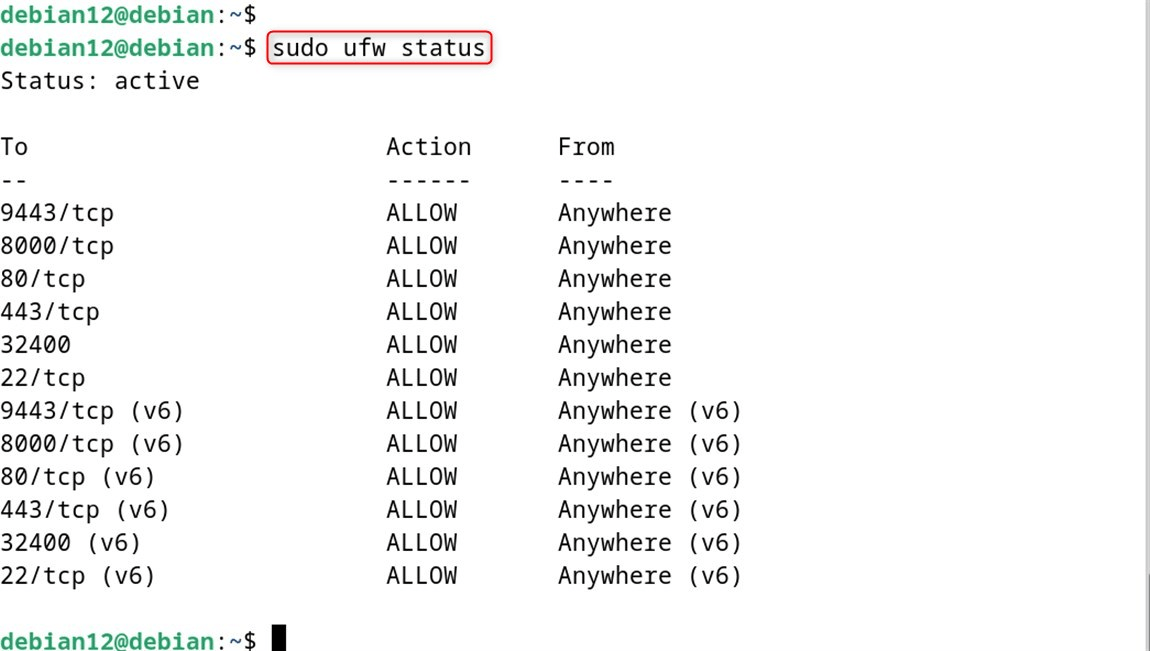
Issue 3: SSH Access Lost
If you lose SSH, physically access the server to turn off UFW:
sudo ufw disable
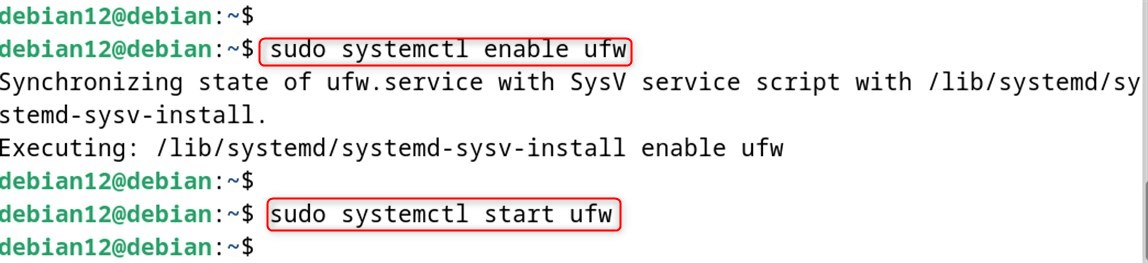
Issue 4: UFW Not Starting at Boot
Allow UFW service at boot time:
sudo systemctl enable ufw
sudo systemctl start ufw
Best Practices for UFW on Debian 12
- Always allow SSH before enabling UFW if you’re working remotely
- Test your rules before applying them to production systems
- Keep logs enabled for monitoring: sudo ufw logging on
- Regularly review your rules: sudo ufw status numbered
- Use specific port numbers instead of service names when possible
- Document your firewall rules for future reference
Conclusion
To install UFW (Uncomplicated Firewall) on Debian 12, you can use the apt package manager. First, update your package lists, then install the ufw package. You can easily install UFW on your Debian 12 server; there are a few ways to achieve it. APT package manager is my recommendation for anybody, basically because it’s straightforward and fits the Debian package system. Once installed, ensure that you properly configure the UFW and add rules to DISALLOW ALL traffic through it.







Leave feedback about this